By: Charles Randolph, PPS & Chuck Tobin, CTM
The executive protection community often reflects on the value we bring to our principals and those that surround them. External observers sometimes view our industry as narcissistic and egotistical operators pining to be caught posing next to a celebrity. People in the industry may even hold this thought. Regardless, the EP community regularly discusses our image’s impact on a protectee. We evaluate how our actions could impact our client’s risk. Hence, in this article, we will discuss the insider threat and EP.
Unfortunately, incidents in the news over the past few years have highlighted our vulnerabilities. If not adequately delivered, close protection can increase the risk to persons receiving security services.
Although contrary to common sense, incidents of executive security professionals bribing officials, intimidating persons of concern, and the like do exist. The industry is rallying to elevate the ethical delivery of services it offers. Still, there are opportunities to reflect on other risks present in the industry we ― as with many sectors ― need to address. Chief among them is Insider Threat.
The Issue
Traditional definitions related to insider threat have focused on an authorized individual’s access and misuse of systems. This includes downloading data they should not collect. It also entails sharing it in a way that harms the individual or organization.
As protectors, we also understand that insider threat risks regarding espionage, sabotage, or the compromise of sensitive information do not purely evolve from access to systems but incorporate the individual’s access to information. These persons are likely not inhibited by traditional cyber defense policies since they may already have access as trusted users.
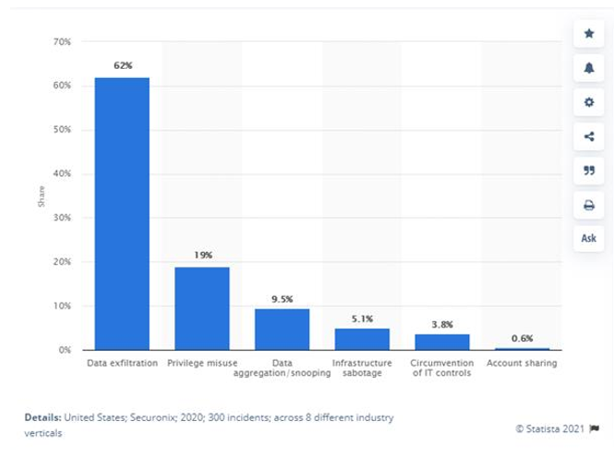
The protector is effectively that trusted user with access and in all other frameworks fits the essential insider threat framework. They just do so from a variety of unique dimensions. These people sit in the front right seat of the car and are privy to sensitive conversations.
They may carry their principal’s devices or private documents. Undoubtedly, few people in the security industry have greater access to information than those in executive protection. The agent has access to critical information, including personal, professional, and family.
They hear business conversations, sensitive research and development discussions, daily itinerary briefings, and even crucial staffing reviews. However, how often do we hear about the executive protection team’s involvement in an “insider threat program?”
If any sector should suggest they have a robust insider threat plan, it should be the executive security community. Many seriously consider this issue. Yet, a large portion of the industry does not invest in examining insider threat risks. They disregard training, monitoring, or investigating concerning activities.
Is this surprising or part of the evolution of our industry?
Protectors and Insider Threat
We can go as far back as Roman emperor Aurelian’s assassination by the Praetorian guard in 275 AD. Or think about the more unsavory slew of Hollywood bodyguards. And even information leaks surrounding Brittany Spears, Brad Pitt, or Angelina Jolie’s private details.
We have witnessed insider threats originating from those trusted to protect. As an industry, we must be proponents of positive change, beginning with an honest assessment about how well we protect our principals and the organizations they represent from an insider threat aspect.

As we evolve as an industry and better define our ethics and best practices for screening close protection personnel, we must also reflect on what type of insider threat program we maintain. People change, situations change, the executive protection professional you hired several years ago has changed.
Have those changes resulted in changes in their perception about their position in life, changing tolerances regarding their financial status and what they deserve, or simply an overall complacency regarding their work? If we do not monitor carefully, we may find ourselves exposing those we wish to protect through intentional action or carelessness.
Kim Kardashian’s bodyguard Pascal Duvier’s removal of all mentions of her from his social media site suggested perhaps he too reflected on the risk created due to his posting of seemingly useless information. As we know, however, the removal of information does not remove that data from the internet. Therefore, there is no getting it back once it is out there.
Insider Threat Program Considerations
While not easy, establishing an insider threat program can be done, and it must consider scale, size, and the dynamic nature of operations. Many publications exist which define and outline the construction of an insider threat program, although they center around digital risks.
The challenge is to create programs that are: coordinated, risk-based, holistic, and proactive, as outlined by Dr. Michael G. Gelles in Insider Threat – Prevention, Detection, Mitigation, and Deterrence.
Coordinated in that someone is ultimately responsible while still having access to stakeholders essential to the program.
Risk-based suggests the program focuses on the key indicators and is aware of the unique issues presented because of the intimate access protectors have.
Holistic in that the program delivers a comprehensive approach to prevention, detection, mitigation, and deterrence, as Dr. Gelles’s book title suggests.
Establishing a Baseline
Ultimately, the program is proactive in managing evolving threats effectively and as early as possible. Like workplace violence and behavioral-based threat management program, a comprehensive insider threat program must monitor activities to assess them and design effective early intervention management strategies.
As the phrase states, “we must collect the dots in order to connect them.” Thus, to best understand a protector’s vulnerability — to compromise, we must first understand what is at risk.
As with many programs, the risk assessment is the essential first step. In the case of Insider Threat, examining an Operational Security (OPSEC) appraisal process is informative:
- Identify Critical Information and Indicators
- Conduct a Threat Assessment
- Implement a Vulnerability Analysis
- Conduct the Risk Assessment
- Apply Appropriate OPSEC Countermeasures
We can already identify Critical Information and Indicators: Everything we touch!
Seriously, examining the types of information our team has access to is an excellent first step and should include our activities, capabilities, and limitations. It should also encompass the data our client possesses, which could be sensitive.
This exercise will highlight a few considerations: what information does the entire team need to know vs. what information should be limited to a select few?
This proven method within an OPSEC assessment examined through an insider threat lens will support determining what information and data we are protecting, who we are protecting it from, why it is so vulnerable, what risks are evident, and mitigation steps.
Further, it will allow us to identify critical information (and perhaps telemetry) that must stay confidential. Imagine the heart-stopping moment when a celebrity’s agent or a corporate executive watches media spillage as a former bodyguard reveals information concerning their client’s very personal lifestyle.
“Must-Haves”
Whether corporate or private, executive protection practitioners must engage in activities that diminish insider threat risk. Remember that some risks result from carelessness while others are intentional. Therefore, a program that informs and reminds practitioners of their obligations and consequences for failing them is essential to its strategy.
Simply having them sign a Non-Disclosure Agreement is not enough. Some additional (and manageable) steps include:
- Establish insider threat policies within your organization and specifically address the executive protection effort.
- Ensure that a data and governance policy exists on collecting, classifying, and keeping information.
- Provide disclosure that monitoring within regulatory limitations will occur and that they may be asked to voluntarily allow access to view private social media sites they participate in.
- Conduct periodic and random inspections of personnel profiles and reinvestigations, like the maintaining of a government clearance.
- Deliver training and education that informs protective personnel of their obligations related to confidentiality. Even after separation from employment and as part of any off-ramping process.
Trust is Key
This is part of the maturation and evolution of the protection industry as it grows and continues to be part of more significant risk discussions. Our profession is based on trust.
To secure it, we must ensure that those who retain our services have no reason to doubt—proactively addressing a practitioner’s role in the Insider Threat continuum highlights that trust and the industry’s understated role in risk leadership.
“Whenever a man does a thoroughly stupid thing, it is always from the noblest motives” – Oscar Wilde, The Picture of Dorian Gray.
Suggested Reading
-
- “Insider Threat: Prevention, Detection, Mitigation, and Deterrence” by Dr. Michael Gelles
- “The CERT Guide to Insider Threats: How to Prevent, Detect, and Respond to Information Technology Crimes” by Dawn Cappelli, Andrew Moore, Randall Trzeciak
- “Insider Threats (Cornell Studies in Security Affairs)” by Matthew Bunn & Scott D. Sagan
- “Tackling the Insider Threat” by Nick Catrantzos, CPP






