In an increasingly interconnected and yet polarised world, in which the economy is in decline and the cost of living in many regions increases, it will be big business that the media blame. This blame culture in which the turnovers of global brands — along with the salaries and bonuses of the CEOs — are published incites real threat and greater hostility towards the senior executives of the world.
The hostility towards these executives and their families will create an avalanche of unwanted attention. The method of communicating that hostility will be varied. Yet, typically it will include:
- letters,
- phone calls,
- emails, and
- social media.
The vast majority of that unwanted communication will be abusive and generally hostile. Still, how do those tasked with keeping them safe eliminate the noise and find the real threat?
The topic of how public figures, the prominent and the wealthy, are targeted has been subject to much academic rigour.
What is known is that there are clear indicators and patterns of human behaviour that can indicate an escalation of a threat. This subject should be vital to any professional tasked with protecting a principal. In this article, we will discuss some of the most significant indicators.
The reality is that many security professionals will be unaware of the real threat communicated to the principal, and there are two significant reasons for that.
Firstly, the person tasked with being the principal’s gatekeeper (the person who reads the communications received) is unlikely to be familiar with the threat indicators. Therefore, this person cannot alert the security professional to any concerns. In fact, truth be known, the communications of problems are likely to be dismissed as nonsense and deleted.
Secondly, very few security professionals are sighted on these indicators. Thus, they are equally unable to identify them.
Origins of the Methodology: The Real Threat
There are generally accepted to be eight behavioural indicators and several key linguistic ones. None of the indicators, individually or collectively, will guarantee that an attack is imminent. What they should do is draw attention to a particular individual from the masses that require additional attention. It is, in some regards, a triage system. Simply put, it enables those persons of concern to be then passed to a specialist for further investigation.
These indicators were initially identified during a research project known as the Exceptional Case Study Project, in which full and open access to 50 years’ worth of US Secret Service files was made available to the researchers with the task of operationalising their findings. As a result, their research has been added to by others who have either corroborated or added to their conclusions.
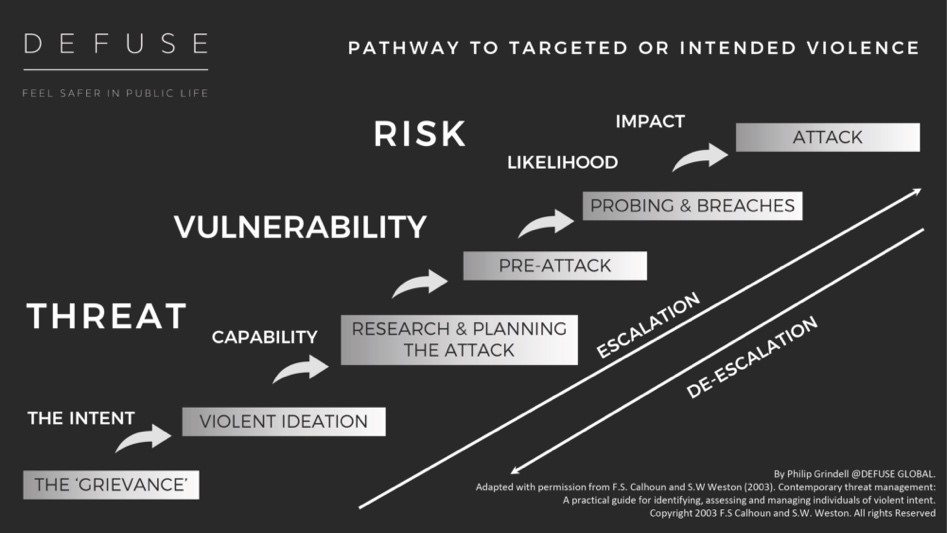
The Pathway to Targeted or Intended Violence
The people of concern are usually those who have become pathologically fixated, meaning that they think of nothing else from the moment they wake up until they go to sleep at night. Research has indicated that people who pursue the rich and famous pose a greater risk of death or severe injury to their targets than do terrorist groups or criminals and are often unperturbed by protective security measures.
Those persons of concern who pose a physical threat rarely just snap. Instead, they follow a process and become predators. The good news is that this process is referred to as the Pathway to Intended Violence. They leave clues.
They are driven by some form of grievance, which can be personal or ideologically motivated, such as activists. This is where their intent is formed. When their grievance fails to be resolved, and they believe they have exhausted all means of doing so, they form their violent ideation.
This is often leaked through linguistic indicators in their communications, and it is critical that both the protectors and the personal assistant are familiar with this. This second indicator is known as ‘end of tether’ or ‘last resort language’ and can be seen in their communications or social media posts. It can be seen as a sign of desperation or distress and examples of which include:
- “You leave me no other option.”
- “I have no choice.”
This indicator suggests that the person of concern is expressing that they must act, and they must act now. It is often time-imperative and a hugely important indicator.
Separating the Real Threat From the Noise
One of the striking facts identified was that with very few exceptions, those individuals who communicate threats directly to the principal don’t pose a physical threat. As a result, this indicator is often referred to by the term ‘Hunter and Howlers’ after wolves.
Those familiar with wolves in the wild will be aware that when you can hear wolves, they are communicating, and when they are hunting, they do so in silence. Whilst it might seem obvious that a person who plans to attack is unlikely to warn their intended target, it is still prevalent for security details to be increased on receipt of a direct threat. This is mistaken for two reasons.
Firstly, as has been stated, those who make such a threat rarely (if ever) attack. Secondly, the increased security has a byproduct of increasing the anxiety of the principal and their family.
The exception to this indicator is when there is a pre-existing personal relationship between the principal and the person of concern. This also includes the scenario where the person of concern is fixated on the principal and believes that there has been a relationship or could be one. In their mind, their delusions are real and must be treated as such.
Research and Planning
Because these people of concern are pathologically fixated, they spend a lot of time researching the target, their lifestyle and plans. Then, they will often make an approach, even engaging with the residential or perimeter security, craving proximity but also testing the security and identifying vulnerabilities.
Whilst many have significant mental illnesses, it would be a mistake to dismiss them as being ‘mad’ and unable to form a rational plan of attack. It is for this reason that briefings and debriefings are vital.
Identification
As has been mentioned, the person of concern will spend a significant amount of time conducting research. However, whilst that research will include their intended target, they also become fixated on previous attackers and assassins.
They will take both inspiration and learn lessons from their attacks, in some cases copying apparently insignificant details. For example, the book “The Catcher in the Rye” has been associated with several fixated attackers after John Lennon’s assassin, Mark Chapman, not only sought to change his name to the main character but was then found to be in possession of the book.
This was mirrored by Reagan’s attacker, John Hinkley Jnr, who was also found to be in possession of the book, as was Robert John Bardo, who murdered Rebecca Schaeffer. He was carrying the book when he visited Schaeffer’s apartment in Hollywood and murdered her. Hinkley admitted that he had studied Chapman.
Leakage
A further indicator commonly experienced is when the person of concern leaks their intentions. This contradicts the previous indicator about directly threatening but is quite different. This indicator has been seen in school shootings, political attacks, and many others.
My personal experience of preventing an attack on a British politician involved the person of concern leaking his intentions to his associates. This can be found online when a student posts a message such as ‘Don’t go to school tomorrow, they are going to pay’ or ‘Watch the news, I’ll be on it tomorrow.’
Any evidence of leakage must be taken seriously, followed up, and shared with law enforcement.
None of the indicators is predictive. Instead, they are preventative indicators that require further investigation by a specialist.